BuildCTF 2024 Reverse
babyre
一个简单的check_debugger,后面把flag分为了两部分,前23是异或0xA,后23是第一个字节异或'-',也就是前23的最后一个,然后后面字节不断异或前面的字节。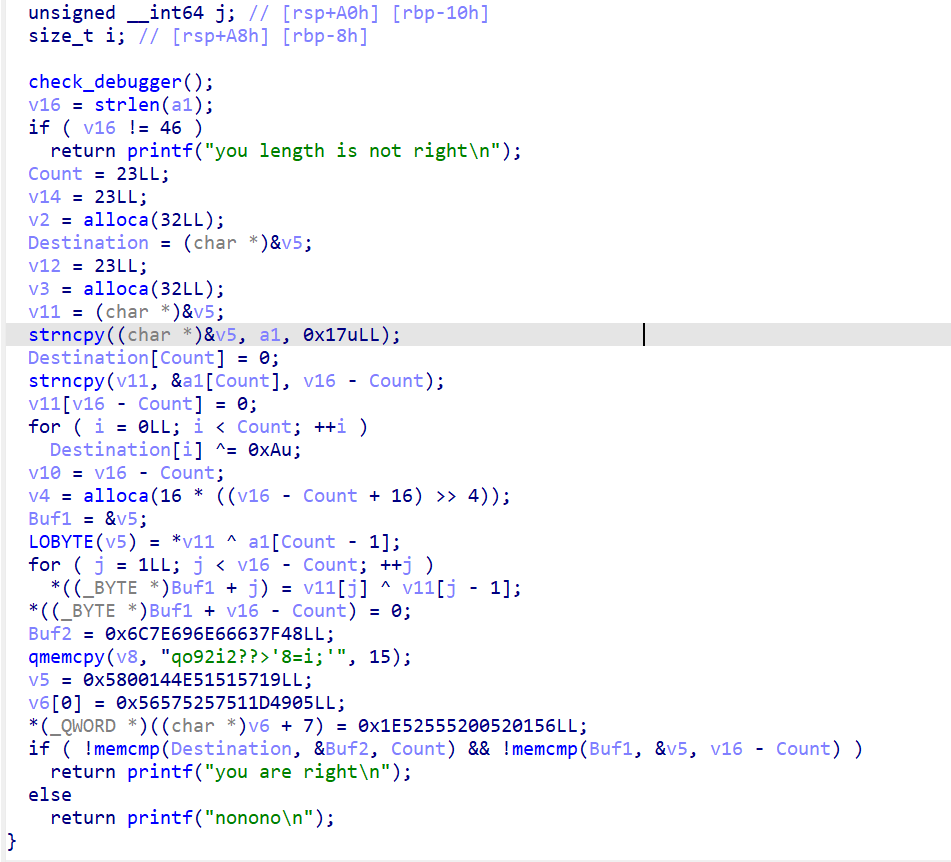
手动解密一下就OK
ez?否
动态加载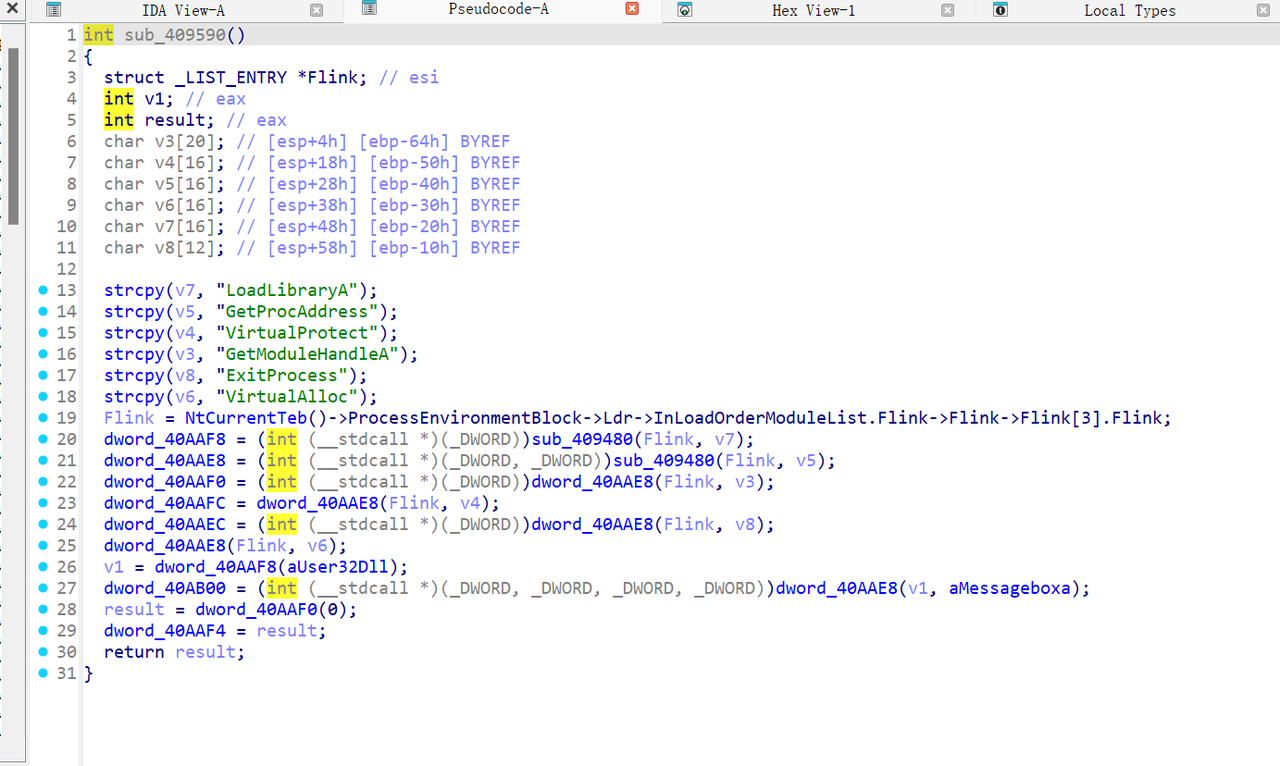
xdbg载入后直接搜字符串,定位到后找到一个xxtea
但是魔改了一些🤬,动调抓一下key,后面还有个..base64标准编码,然后动调也能看见结果。
from regadgets import *
def b2024buildctf(z, y, sum, k, p, debug = False):
e = (sum.value >> 2) & 3
PE = (p & 3) ^ e
Ly = y.value << 3
Ry = y.value >> 7
Lz = z.value << 8
Rz = z.value >> 5
LzRy = Rz ^ Ly
LyRz = Ry ^ Lz
SY = sum.value ^ y.value
K = k[PE].value
KZ = K ^ z.value
result = (LzRy + LyRz) ^ (KZ + SY)
return result
xxtea_key = b'Yigod' + b'\x00' * 11
enc = decode_b64('DcxHei12cHzBv7QrvkVO693GezASEOK8PF3rZzvfJNYihLczydjCBBYN1LF9JU0hw0gULw==')
ee = xxtea_decrypt(byte2dword(enc), byte2dword(xxtea_key), delta=0x11451411, shift_func=b2024buildctf)
print(dword2byte(ee))
# b'BuildCTF{Life_long_long&&debugging_15_wonderful}0\x00\x00\x00'ez_asm
看题目猜到了是idct和dct,然后找一下有个memcpy,肯定是把加密数据复制了一份,然后在最下面找到加密后的数据,然后idct就可以了。
from regadgets import *
enc = [0x4E,0x7B,0x4A,0xCE,0x89,0x69,0x80,0x40,0xB5,0xDF,0xDA,0x89,0x92,8,0x2E,0x40,0x3D,0xEF,0xC6,0x82,0xC2,0xD0,0x3E,0xC0,0x43,0x3B,0xA7,0x59,0xA0,0xBD,0x3A,0x40,0xA7,0x5B,0x76,0x88,0x7F,0xD8,0x2E,0x40,0xE4,0x12,0x47,0x1E,0x88,0x5C,0x1F,0xC0,0x3D,0x82,0x1B,0x29,0x5B,0x28,0x40,0x40,0x65,0x8C,0xF,0xB3,0x97,0xC3,0x43,0xC0,0xA0,0x17,0xEE,0x5C,0x18,0x29,0x29,0x40,0xEC,0x13,0x40,0x31,0xB2,0xC6,0x47,0xC0,0x16,0xDB,0xA4,0xA2,0xB1,0x8E,0x38,0x40,0xB6,0xA2,0xCD,0x71,0x6E,0xB3,0x1E,0xC0,0xD2,0xC5,0xA6,0x95,0x42,0x4E,0x46,0xC0,0x8F,0x37,0xF9,0x2D,0x3A,0xB1,0x39,0xC0,0xD7,0x16,0x9E,0x97,0x8A,0x79,0x37,0xC0,0x22,0x89,0x5E,0x46,0xB1,0xE0,0x34,0x40,0xAE,0xF,0xEB,0x8D,0x5A,0x8D,0x31,0x40,0xFD,0xF8,0x4B,0x8B,0xFA,0x24,0x1A,0xC0,4,0x75,0xCA,0xA3,0x1B,0xA1,0x1E,0x40,0x93,1,0xA0,0x8A,0x1B,9,0x48,0xC0,0x33,0xDF,0xC1,0x4F,0x1C,0x28,0x21,0x40,0x2A,0xE5,0xB5,0x12,0xBA,0xDF,0x41,0xC0,0x16,0x32,0x57,6,0xD5,0x86,0x1E,0x40,0x7C,0x65,0xDE,0xAA,0xEB,0xDC,0x39,0x40,5,0xA3,0x92,0x3A,1,0x4D,0x16,0x40,0xE4,0x4A,0x3D,0xB,0x42,0xF9,0x46,0xC0,0xA4,0x50,0x16,0xBE,0xBE,0x66,0x40,0xC0,0xD5,0x42,0xC9,0xE4,0xD4,0xDE,0x12,0xC0,0xEB,0x6F,9,0xC0,0x3F,0x45,0x30,0x40,0x1C,0x95,0x9B,0xA8,0xA5,0x69,0x1F,0xC0,0x3F,0x39,0xA,0x10,5,0xF3,0xF3,0x3F,0x11,0xA6,0x28,0x97,0xC6,0xF,0xB,0x40,0xA,0x66,0x4C,0xC1,0x1A,0x67,0x3E,0x40]
encd = byte2double(enc)
# 525.192, 15.0167, -30.8155, 26.7407, 15.4228, -7.84036, 32.3153, -39.5281, 12.5803, -47.5523, 24.5574, -7.67523, -44.6114, -25.6923, -23.4748, 20.8777, 17.5522, -6.53611, 7.65733, -48.0712, 8.57834, -35.7479, 7.63167, 25.863, 5.5752, -45.9473, -32.8027, -4.71761, 16.2705, -7.85317, 1.24683, 3.3827,30.4028
decrypted_values = idct_transform(encd)
print(bytes(decrypted_values))
# b'BuildCTF{H0vv_w0ndevfUl_arm&&DTC}'晴窗细乳戏分茶
一个tea一个xtea,直接解密。
from regadgets import *
key = [1] * 4
enc = [1] * 6
key[0] = 1646625
key[1] = 164438
key[2] = 164439
key[3] = 2631985
enc[0]=-1559465970
enc[1]=-158607645
enc[2]=-1059812880
enc[3]=314506021
enc[4]=-2131835469
enc[5]=731233488
r = b''
r += tea_decrypt(enc, key=key, delta=-0x61C88647)
key2 = [1] * 4
enc2 = [1] * 4
key2[0] = 358040470
key2[1] = 1131796
key2[2] = 85988116
key2[3] = 120935944
enc2[0] = -2022820316
enc2[1] = -1470027656
enc2[2] = 1057529116
enc2[3] = 1243942236
r += xtea_decrypt(enc2, key=key2, delta=-0x61C88647)
print(r)
# b'BuildCTF{D0_y0u_WanT_T0_D3ink_s0mE_TEA?}'自是花中第一流
看题目可以猜到是花指令,ida打开手动patch一下 jnx 和 jx两个连起来和后面的一个0xE8就可以了。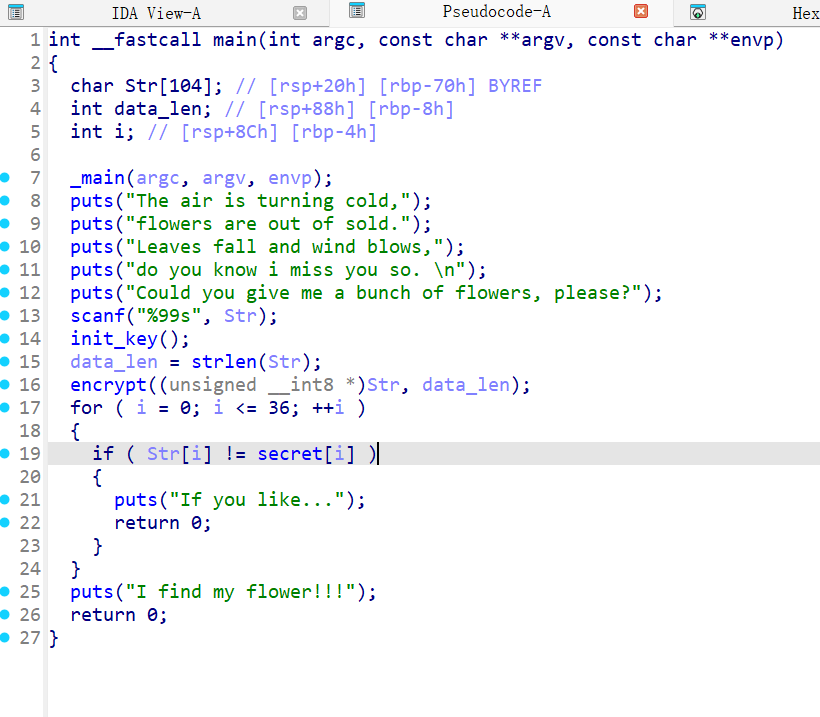
可惜secret是init_key里面生成的,init_key也有花,我们直接去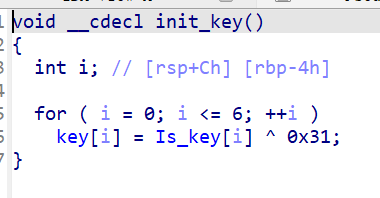
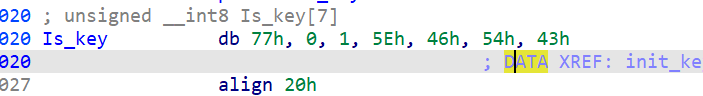
后面还有个encrypt,没花,一眼标准rc4了
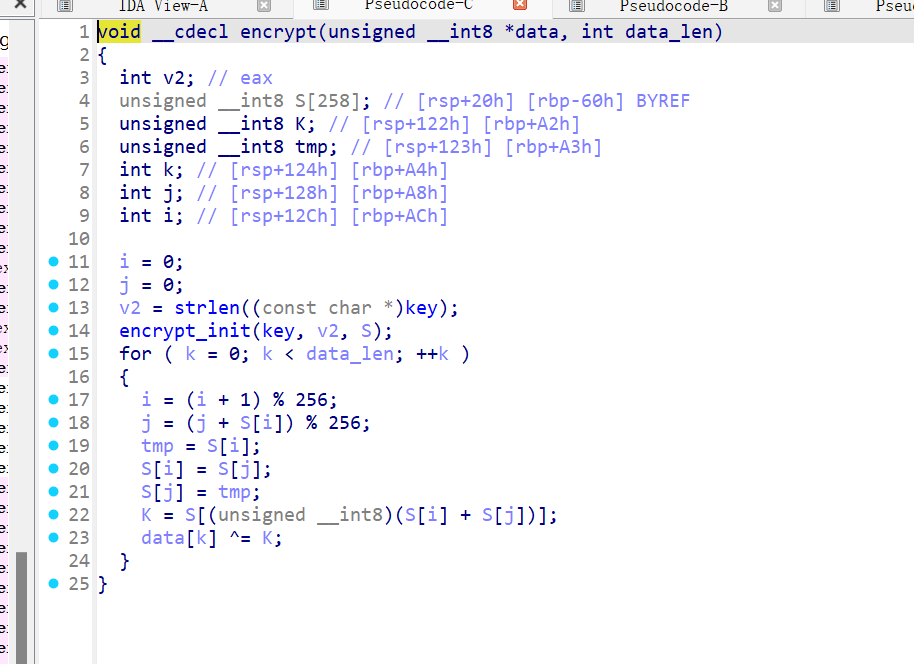
from regadgets import *
enc =[0x7E, 0x58, 0x36, 0xF5, 0xC5, 0xF3, 0x39, 0xD4, 0x65, 0xCF, 0x67, 0x85, 0x37, 0x8C, 0x0C, 0xD4, 0x46, 0x88, 0x95, 0x2F, 0xDB, 0xB6, 0xA7, 0x56, 0xDC, 0xFE, 0xA9, 0x99, 0x92, 0x60, 0xA6, 0xC9, 0xE7, 0xCF, 0xBD, 0xB5, 0x62]
ik = [0x77, 0x00, 0x01, 0x5E, 0x46, 0x54, 0x43]
key = bxor_cycle(ik, b'\x31')
print(rc4_crypt(rc4_init(key), enc))
# b'BuildCTF{What_A_Beautifu1_F10ower!!!}'新?Android路
AndLua
but.lua->RC4重新打包,随便找个工具都能反编译
crc3264.lua -> 疑似变表Base64,但是不会反编译
native->AndLua库,没有修改,所以不用看
上面几个lua都有一个base64编码,网上找AndLua解密就可以。
由于crc3264没法反编译,所以我们把main.lua更换,print一下
我们构造一个特殊的字符串组合,用来套出Base64表。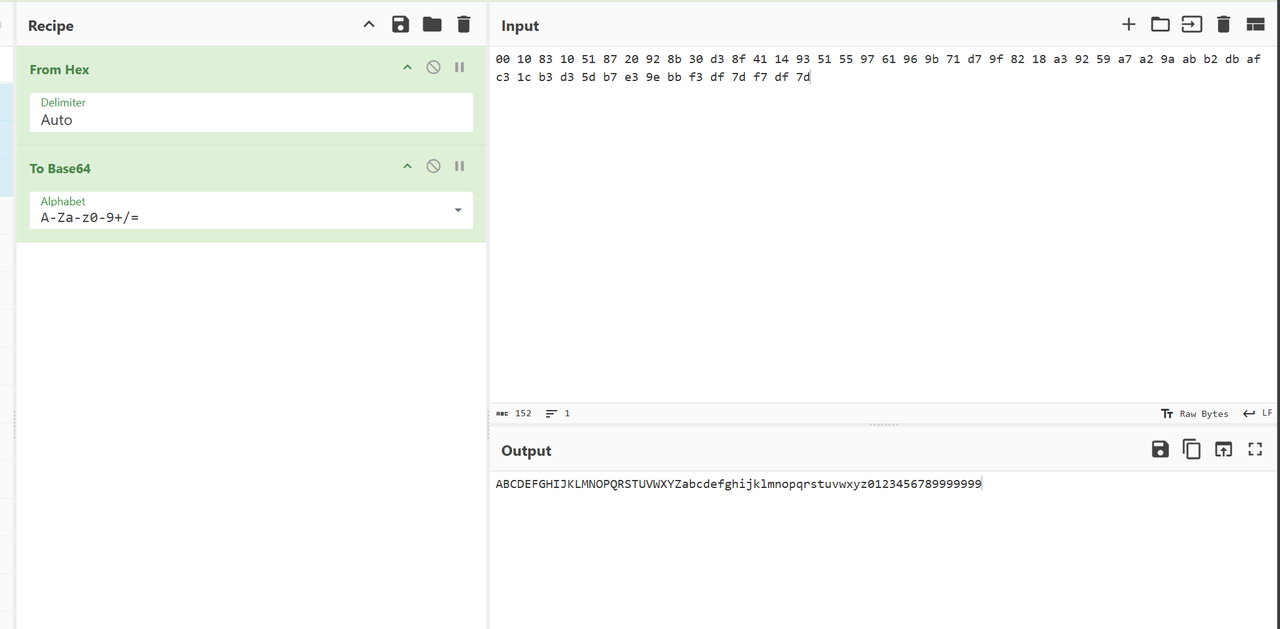
local str ="\x00\x10\x83\x10\x51\x87\x20\x92\x8b\x30\xd3\x8f\x41\x14\x93\x51\x55\x97\x61\x96\x9b\x71\xd7\x9f\x82\x18\xa3\x92\x59\xa7\xa2\x9a\xab\xb2\xdb\xaf\xc3\x1c\xb3\xd3\x5d\xb7\xe3\x9e\xbb\xf3\xdf\x7d\xf7\xdf\x7d"
local result = L1_2.crc3264.encode(str)
print(result)
-- AbCdEfGhIjKlMnOpQrStUvWxYzaBcDeFgHiJkLmNoPqRsTuVwXyZ0246813579999999重打包回去后运行可以得到表:
AbCdEfGhIjKlMnOpQrStUvWxYzaBcDeFgHiJkLmNoPqRsTuVwXyZ0246813579+/
用CyberChef解
#recipe=From_Base64('AbCdEfGhIjKlMnOpQrStUvWxYzaBcDeFgHiJkLmNoPqRsTuVwXyZ0246813579%2B/',true,false)RC4(%7B'option':'UTF8','string':'BuiIdCTF'%7D,'Latin1','Latin1')From_Base64('AbCdEfGhIjKlMnOpQrStUvWxYzaBcDeFgHiJkLmNoPqRsTuVwXyZ0246813579%2B/',true,false)&input=TDh4ZUc5MmErbXJscWE4QnA1NGZ4VGdBZTdJSnVlNUhUWngrYk02ZUJ4SnIwdWtSNm9RblJnPT0&oeol=CRBuildCTF{vve1C0me2_lua_word}
Pyc
import base64
def decode(encoded_message):
decoded = base64.b64decode(encoded_message)
message = ""
for i in decoded:
x = i - 16
if x < 0:
x += 256
x = x ^ 32
message += chr(x)
return message
correct = 'cmVZXFRzhHZrYFNpjyFjj1VRVWmPVl9ij4kgZW0='
print(decode(correct))
# BuildCTF{pcy_1s_eaey_for_Y0u}ez_vm
慢慢调试跟数据变化就行。
from z3 import *
enc = [0x0000054A, 0x00005541, 0x00000665, 0x000066D5, 0x00000768, 0x00000769, 0x00000786, 0x000078EA, 0x00000787, 0x000078ED, 0x000006BF, 0x00006C63, 0x00000553, 0x000055C4, 0x000005F7, 0x00005FD9]
result = ''
for i in range(0, len(enc), 2):
b = chr((enc[i+1] - ((enc[i] >> 4) | enc[i] << 4)) & 0xff)
a = chr((enc[i] - ((ord(b) >> 4) | ord(b) << 4)) & 0xff)
result += a + b
print(result)
# vMp_1s_r0u9h_ORZezMfc
Spy++查句柄,然后伟大的易语言+CE搜
BuildCTF{WindowsApi_is_easy!!!}
ez_xor?
实际上和xor没什么关系,输入一组数据,看变化就行了。
from regadgets import *
from z3 import *
after = b"\x45\x55\x91\x0B\xA8\xAE\x10\xE1\x50\x7E\xDE\x11\xFC\xBE\x83\x21\x1C\x35\xA2\x31\x11\x40\x5E\x18\x69\x8F\x7E\x6F\x61\x45\x3E\x75\x1E\x4C\x25\x37\xD5\xB4\x74\x43\x9E\x93\x44\xB6\xC7\x8B\x84\xAA\xBF\xDA\x1A\x1E\x6A\x4B\x80\x32\x8C\x0D\xE6\x9F\x99\xB3\x1A\x3A"
raw = b'a'*len(after)
table = [after[i] - raw[i] for i in range(len(after))]
enc = b"\x19\x68\xA2\xEF\x7B\xBA\x0E\xC5\x5D\x80\xEF\x09\x0B\xD1\x81\xF1\xF0\x33\xA6\x11\x23\x58\x5C\x2B\x38\x8D\x80\x60\x61\x27\x48\x35"
for i in range(len(enc)):
print(chr((enc[i] - table[i]) & 0xff), end='')
# 5trE4m_EncrYpt_15_eAsy_t0_cRaCk!notMe
BruteForce sha256
from regadgets import *
from z3 import *
from hashlib import sha256
from itertools import product
from string import printable
sets = "ABCDEFGHIJKLMNOPQRSTUVWXYZ{}-_1234567089abcdefghijklmnopqrstuvwxyz"
def bf_sha256(v):
it = product(printable, repeat=4)
for i in it:
j = "".join(i)
if sha256(j.encode()).digest() == v:
return j
return '****'
enc = [0x79, 0x69, 0x88, 0x3E, 0xA8, 0x1D, 0xCF, 0x11, 0x3D, 0xDC, 0x62, 0xE9, 0xAE, 0xCB, 0x54, 0x86, 0xCB, 0x8C, 0x96, 0x1E, 0x9A, 0x0D, 0xD6, 0x83, 0xF8, 0x85, 0xE5, 0xBD, 0x68, 0x37, 0xAD, 0xDF, 0xDE, 0x58, 0xDC, 0xE0, 0x52, 0x57, 0x69, 0x7E, 0xF2, 0x5C, 0xA5, 0x7A, 0x0B, 0xFA, 0xC8, 0xED, 0x83, 0x89, 0xDC, 0x20, 0x03, 0xBB, 0xA3, 0xAB, 0x4B, 0x6E, 0x95, 0xD5, 0x6F, 0xC7, 0xBA, 0xC6, 0x58, 0x37, 0x55, 0x78, 0xCE, 0xB4, 0x62, 0xF4, 0x53, 0x1A, 0x0E, 0x29, 0x7C, 0xCA, 0x93, 0x71, 0xC9, 0x44, 0xAA, 0x3B, 0xC7, 0x05, 0x14, 0x06, 0xF4, 0xAE, 0xBE, 0x8A, 0x45, 0x3A, 0x58, 0x21, 0xE7, 0xC5, 0xE7, 0x66, 0xDF, 0x33, 0x36, 0x11, 0xC0, 0x3F, 0xF1, 0x25, 0xD2, 0x15, 0x76, 0xD5, 0x9D, 0x0C, 0x9A, 0x01, 0xA5, 0x72, 0xB7, 0x9A, 0x69, 0xE7, 0xDB, 0x82, 0x16, 0x45, 0xD9, 0x77, 0x46, 0xEC, 0x58, 0xDD, 0xC7, 0xFF, 0x28, 0xE3, 0x5C, 0x7D, 0x36, 0x1F, 0x6C, 0xE9, 0xBE, 0xA2, 0xB0, 0x8E, 0xDF, 0x94, 0x3B, 0x22, 0x6E, 0x90, 0x03, 0x47, 0x2B, 0x11, 0x9B, 0xA8, 0xD6, 0xC7, 0x36, 0x09, 0x5C, 0xFF, 0xF0, 0x4A, 0x7E, 0x49, 0x52, 0x30, 0xEA, 0x66, 0x47, 0xA2, 0xFB, 0x0B, 0x75, 0x61, 0xA5, 0x12, 0x73, 0x96, 0xE8, 0xCB, 0x40, 0x28, 0xA3, 0x65, 0x10, 0x1D, 0x18, 0xFD, 0x28, 0x6A, 0x2E, 0x7A, 0x0B, 0xD1, 0xEE, 0xE9, 0x49, 0xF6, 0xE1, 0x28, 0x9D, 0x24, 0x20, 0x90, 0x8D, 0x37, 0xC7, 0xB6, 0x05, 0x2D, 0xCC, 0xA8, 0x96, 0xEA, 0xCD, 0x25, 0x0E, 0x61, 0x12, 0x2C, 0x95, 0x91, 0x11, 0x58, 0x3B, 0xBE, 0x38, 0x46, 0x5D, 0xCF, 0x51, 0xE9, 0x2D, 0x9A, 0xDA, 0xAA, 0x44, 0x20, 0x49, 0x45, 0x74, 0x37, 0x78, 0x12, 0xB3, 0x5B, 0xB0, 0x52, 0x80, 0x8E, 0xED, 0xBA, 0x3B, 0xB9, 0x23, 0x7B, 0x41, 0xB7, 0xC9, 0xA7, 0x85, 0x14, 0xE6, 0x34, 0x5C, 0x6C, 0x65, 0x90, 0x8B, 0x50, 0xF9, 0x73, 0x09, 0xB8, 0xFB, 0xCA, 0xBD, 0x3D, 0xAD, 0x2C, 0x6E, 0x29, 0x9C, 0x63, 0x08, 0x19, 0x33, 0xDC, 0xB1, 0x79, 0xD6, 0x17, 0x41, 0x02, 0x80, 0x21, 0x6D, 0xB8, 0x66, 0x22, 0x09, 0xB9, 0xE1, 0x00, 0x83, 0x97, 0x9A, 0x60, 0xB3, 0x1F, 0x7C, 0xB8, 0xFA, 0x8D, 0xB1, 0xBE]
result = ''
for i in range(0, len(enc), 32):
v = enc[i:i+32]
v = bxor_cycle(v, b'BuildCTF')
result += bf_sha256(v)
print(result)
print(result)
'''
cracking 3b1ce152cc5e9b577fa90b85ca8800c089f9ff72fe4e82c5baf08cd10c74f999
Buil
cracking 9c2db58c36143d38b029cc166fb99cabc1fcb54c67f8f7ed091bfcb90b84ee80
BuildCTF
cracking 1a423c14aaf736b2116f67451889c7378b31c357a3464040b6dbd7e621790c67
BuildCTF{y0u
cracking a5b08e0abb706257824a9849b6562293df79f36dc131e3dc2b92b2ee72068d31
BuildCTF{y0u_4r3
cracking 049931b1a3bc7ca51e085f7308aaeae4f2fbb6f85f613ad64132427dffeb8281
BuildCTF{y0u_4r3_4_g
cracking 747c359394092a0f1045830a23e1af4d3714cc7e17d5bc8d025dca09745e4cbb
BuildCTF{y0u_4r3_4_g00d_
cracking 6a1f47166f92baaf0b838844f96774d6cf42aeda616e98eed49fa4496a22466a
BuildCTF{y0u_4r3_4_g00d_w1nd
cracking d7e478345ffd6c001fba388549d98eec0655202910742c54f12ed93ee4cdb9fc
BuildCTF{y0u_4r3_4_g00d_w1nd0w5_
cracking 79cc4a1725f49de1c7618f58382f31d6c925901f6dfbaf8cff48c4400a6ac825
BuildCTF{y0u_4r3_4_g00d_w1nd0w5_cr4c
cracking 4a6c5ab0d53a82510377e94d09fb32644bcc886ce7d4ce26f16a15d49ecee5f8
BuildCTF{y0u_4r3_4_g00d_w1nd0w5_cr4ck3r}
BuildCTF{y0u_4r3_4_g00d_w1nd0w5_cr4ck3r}
'''