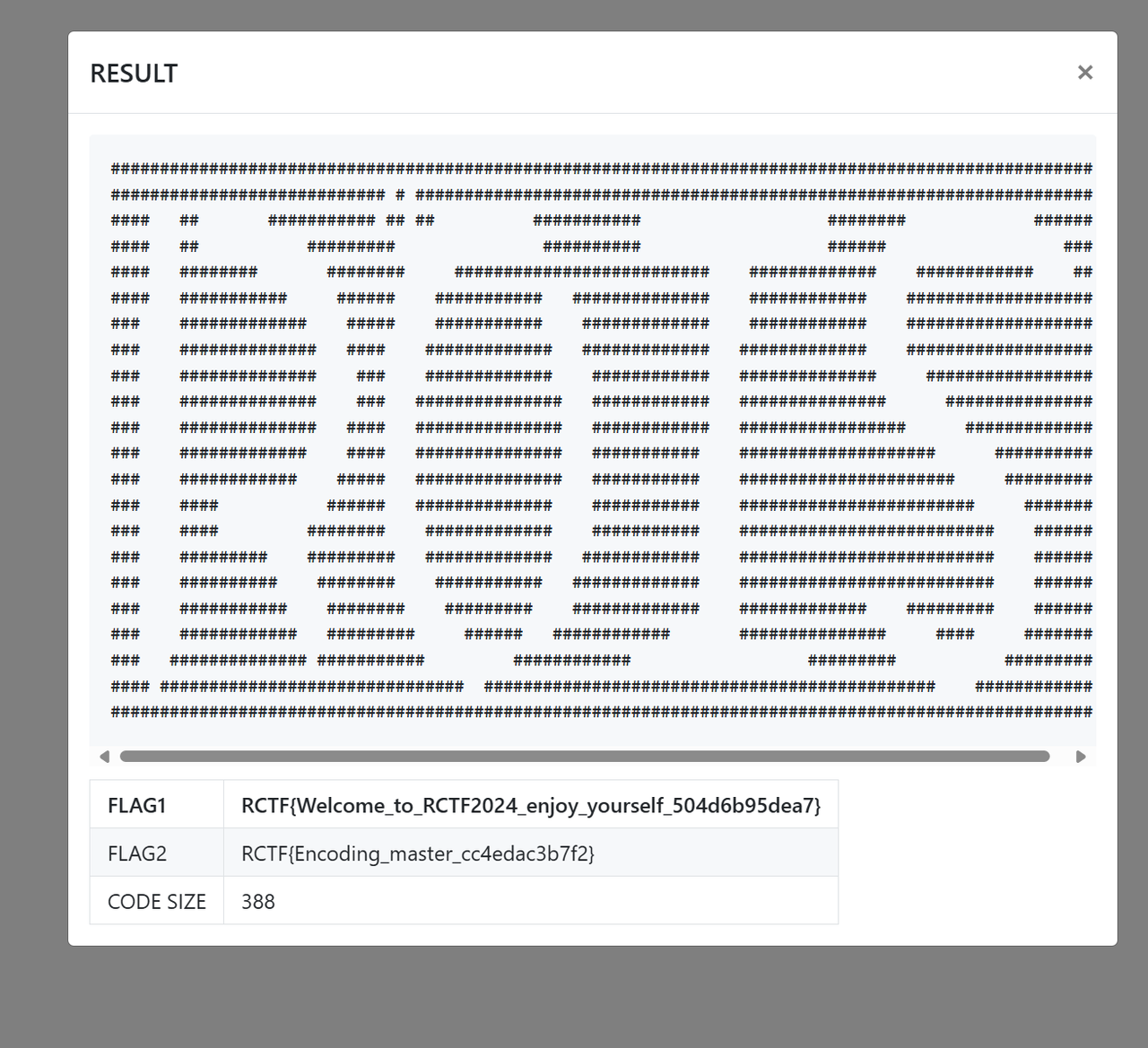
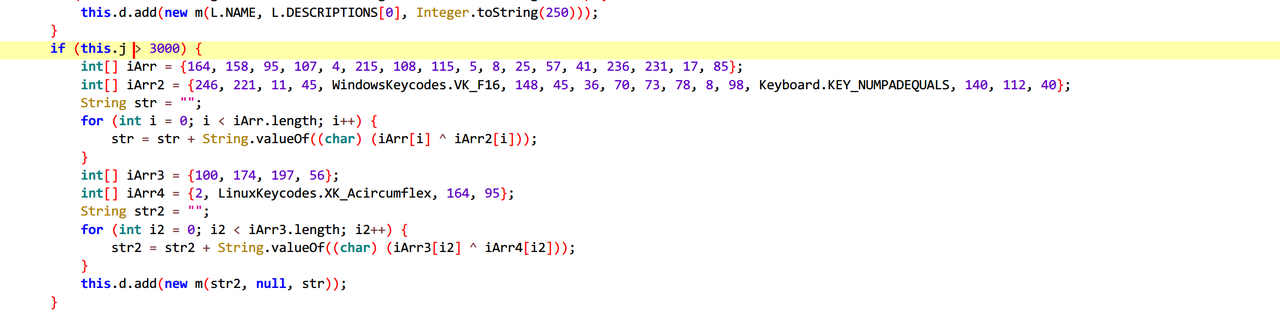
whereThel1b
在kali下运行程序,发现可以运行,然后测试输入,发现长度和base64很像(加新的东西后,长度不一定变长,但是总体稳定增长,且只影响前面后面的结果),构造一个字符串,使得加密后长度和encry数组长度一致,测出来flag长度,测试得到flag{uuid},然后得到xor表(换输入后发现在长度一致的时候xor表一致),然后解密encry,得到flag,不过并没有对so文件进行研究,或者是对trytry上面一个函数研究,就猜出来结果了。
flag{7f9a2d3c-07de-11ef-be5e-cf1e88674c0b}
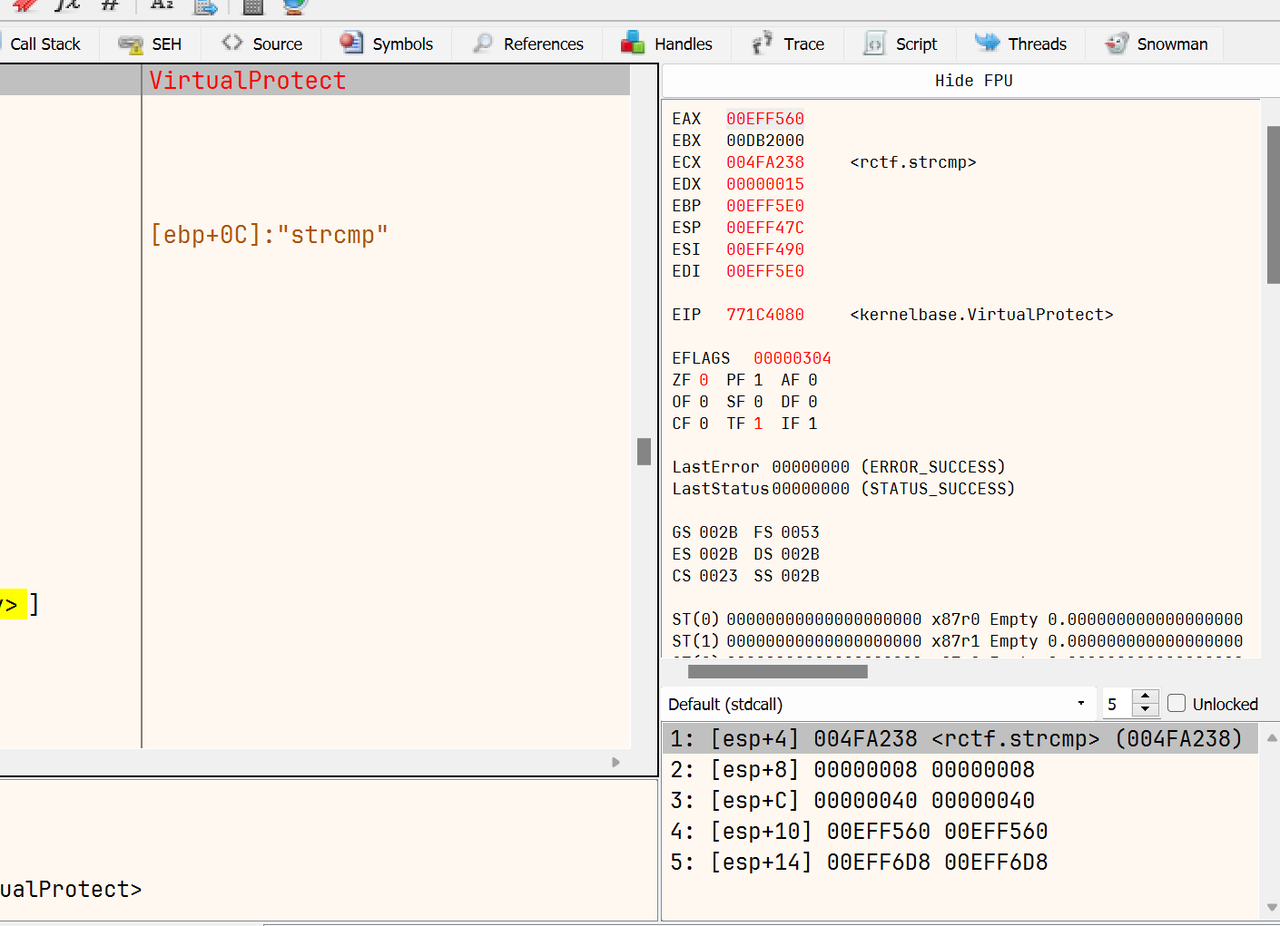
gdb_debug
#include <iostream>
#include <cstring>
#include <vector>
void bur(int seed)
{
srand(seed << (32 - 4));
char result[] = "congratulationstoyoucongratulationstoy";
unsigned char byte_62333B8010A0[40] = {
0xBF, 0xD7, 0x2E, 0xDA, 0xEE, 0xA8, 0x1A, 0x10, 0x83, 0x73, 0xAC, 0xF1, 0x06, 0xBE, 0xAD, 0x88,
0x04, 0xD7, 0x12, 0xFE, 0xB5, 0xE2, 0x61, 0xB7, 0x3D, 0x07, 0x4A, 0xE8, 0x96, 0xA2, 0x9D, 0x4D,
0xBC, 0x81, 0x8C, 0xE9, 0x88, 0x78, 0x00, 0x00
};
char input[] = "flag{2b838a97ade9f743bb07ce476e02804c}";
size_t len = strlen(input);
char* pull1 = (char*)malloc(len);
char* box = (char*)malloc(len);
char* pull3 = (char*)malloc(len);
char r1[38] = {0};
char r2[38] = {0};
char r3[38] = {0};
for (int i = 0; i < len; i++)
{
r1[i] = rand();
// std::cout << "test:r1[i] = " << seed << ' ' << std::hex << (int)r1[i] << std::endl;
}
for (size_t k = len - 1; k; --k)
{
r2[k] = rand() % (k + 1);
}
for (int i = 0; i < len; i++)
{
r3[i] = rand();
}
// Generate
for (size_t i = 0; i < len; i++)
box[i] = i;
// Generate
for (size_t i = 0; i < len; i++)
pull1[i] = input[i] ^ r1[i];
// Exchange
for (size_t k = len - 1; k; --k)
{
//char s = rand() % (k + 1);
char c = box[k];
box[k] = box[r2[k]];
box[r2[k]] = c;
}
for (int i = 0; i < len; i++)
{
pull3[i] = pull1[box[i]] ^ r3[i] ^ byte_62333B8010A0[i];
}
// Decrypt
for (int i = 0; i < len; i++)
{
pull1[box[i]] = result[i] ^ byte_62333B8010A0[i] ^ r3[i];
}
for (size_t i = 0; i < len; i++)
{
pull1[i] ^= r1[i];
putchar(pull1[i]);
}
/*
for (size_t m = 0; ; ++m)
{
if (m >= len)
break;
pull3[m] = pull1[box[m]];
}
// ^ rand() ^ pull1[m]
for (size_t m = 0; ; ++m)
{
if (m >= len)
break;
pull3[m] = pull1[box[m]] ^ r3[m] ^ byte_62333B8010A0[m];
}
*/
// pull3 == congratulationstoyoucongratulationstoy
}
int main()
{
for (int i = 0; i < 15; i++)
{
bur(i);
std::cout << std::endl;
}
return 0;
}
结果是,9,然后flag:
[9�4�_�G�9���v ��,��V�[<�ZQӂ�s�
j���}�p@�o���i�V}{(��5���h�]��+o���Ʉ
5��X:�
&���
�� �0V�O����l<�7��
�7��d�0���q>�;�a��s�EF�6�
���wX�dmL�֜�h|y7�m>4
Xꙟ�����^8�
�(�Uv�K����(J����=/����g��w�_��2��
flag{78bace5989660ee38f1fd980a4b4fbcd}
��:�ó��<���(��7hy�����i�y_f��
oQ�rh^0wLU���>\k��m���7��y�X7��/ƙ@
Ǧ�
p߿9�p�H(���"b��$D�����Z��<GF�
��σ?6���oV^�^w���n����:K@܃�
��C&.�D2_�6�5��~%�X�+�t�+l@ѩ`1�3Ƕ
`��i)��)�b�%��`�g�ݓ�yq�^���B��y�
��mU�r�#�F�.5-}����O"�n�
B��+#d��y��
qFUgrh����;�C��?���1ʐ��}�� #��KF
GoReverse
拿到结果后先base64解密放成hex,
AES Decrypt(key=dPGWgcLpqmxw3uOXhKpKV009Cql@@XE6, iv=dPGWgcLpqmxw3uOXhKpKV009Cql@@XE6)
Mode = CBC
然后SM4 Decrypt (key=pg5g#k6Qo3L&1EzT, iv=上个结果的前32字符) MODE= CTR
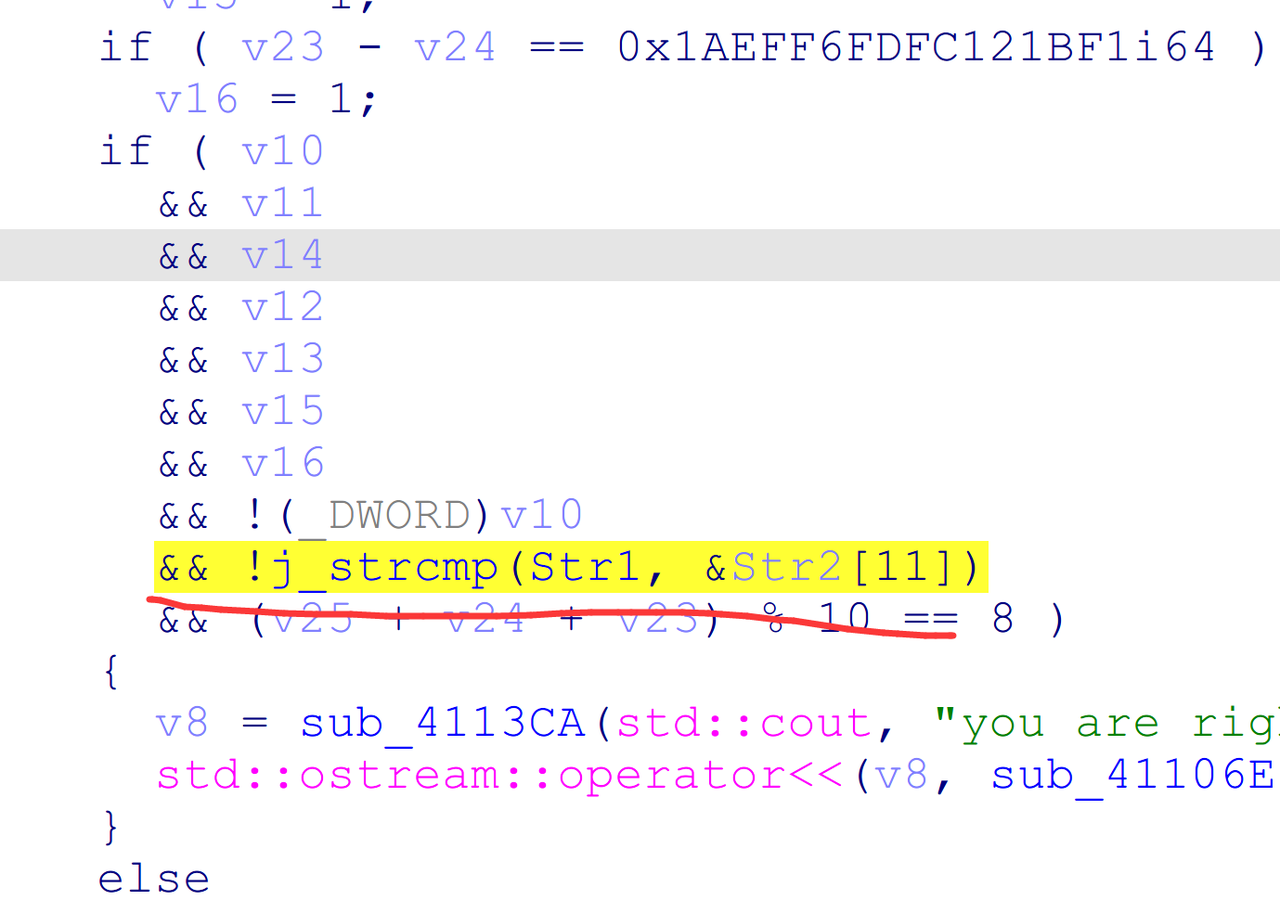
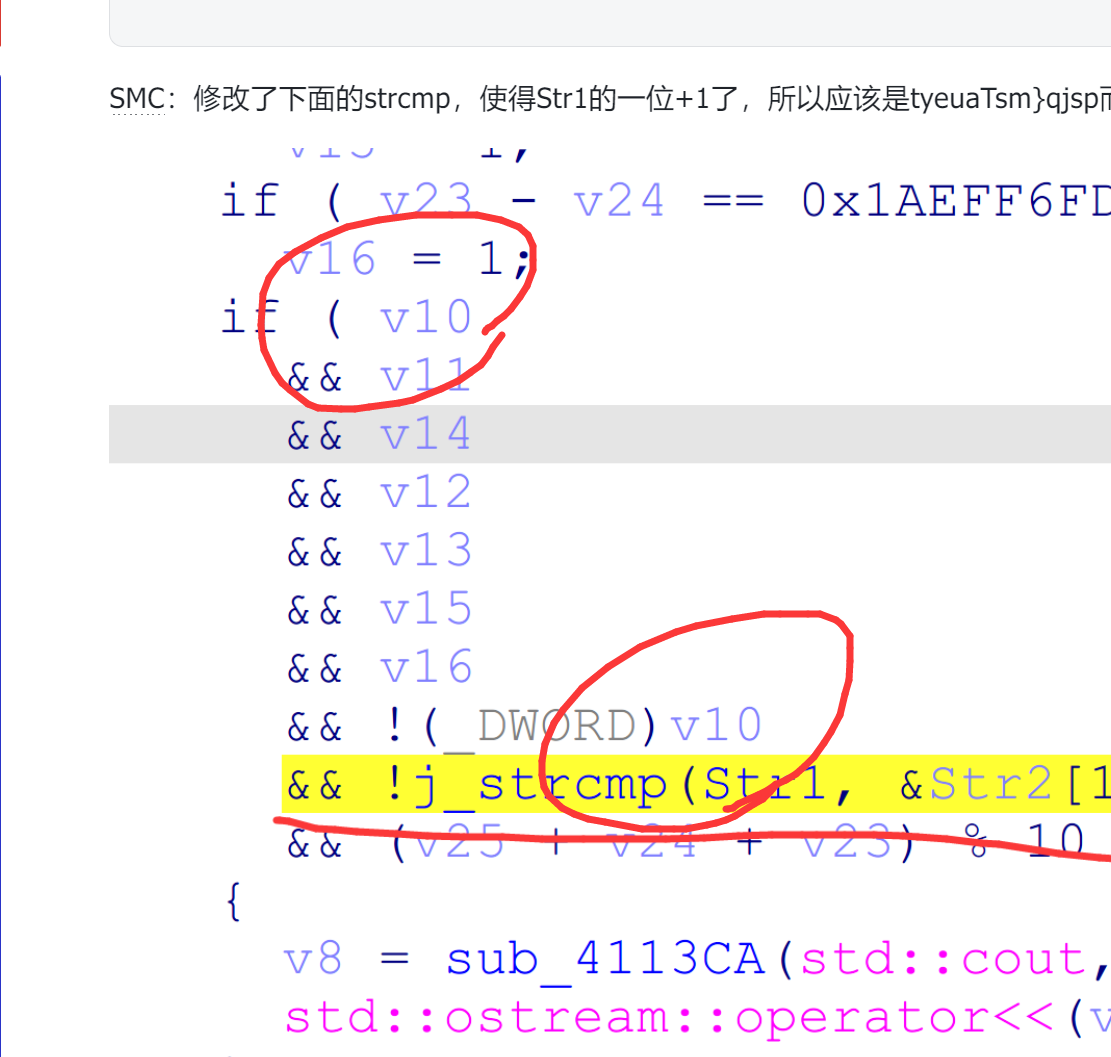
最后是XXTEA(非标准),被更改了delta和mx,逆了3个小时才发现mx被改了。。。
#define MX (z ^ (key[(p&3)^e])) + (sum ^ y ^ (((16 * z) ^ (y >> 3)) + ((z >> 5) ^ (4 * y))))
这是标准的MX
#define MX (((z>>5^y<<2) + (y>>3^z<<4)) ^ ((sum^y) + (key[(p&3)^e] ^ z)))
上面解密的数据
0x6f8c082d,0x91d710f1,0x13cae9c4,0x28640b11,0x61831577,0x07f8bf0a,0xeb9905f0,0x6397b535,0x42237994,0x0d8269de,0x1fb90102
提取出来的key
0x385E7342, 0x345A772A, 0x6F38756C, 0x6B402652
DELTA 0x7fab4cad
网上搜脚本
btea(v, -n, k);
void btea(uint32_t* v, int n, uint32_t const key[4])
{
uint32_t y, z, sum;
unsigned p, rounds, e;
if (n > 1) /* Coding Part */
{
rounds = 6 + 52 / n;
sum = 0;
z = v[n - 1];
do
{
sum += DELTA;
e = (sum >> 2) & 3;
for (p = 0; p < n - 1; p++)
{
y = v[p + 1];
z = v[p] += MX;
}
y = v[0];
z = v[n - 1] += MX;
} while (--rounds);
}
else if (n < -1) /* Decoding Part */
{
n = -n;
rounds = 6 + 52 / n;
sum = rounds * DELTA;
y = v[0];
do
{
e = (sum >> 2) & 3;
for (p = n - 1; p > 0; p--)
{
z = v[p - 1];
y = v[p] -= MX;
}
z = v[n - 1];
y = v[0] -= MX;
sum -= DELTA;
} while (--rounds);
}
}
asm_re
打开后发现是ARM汇编,并且给了一个IDA反汇编的结果
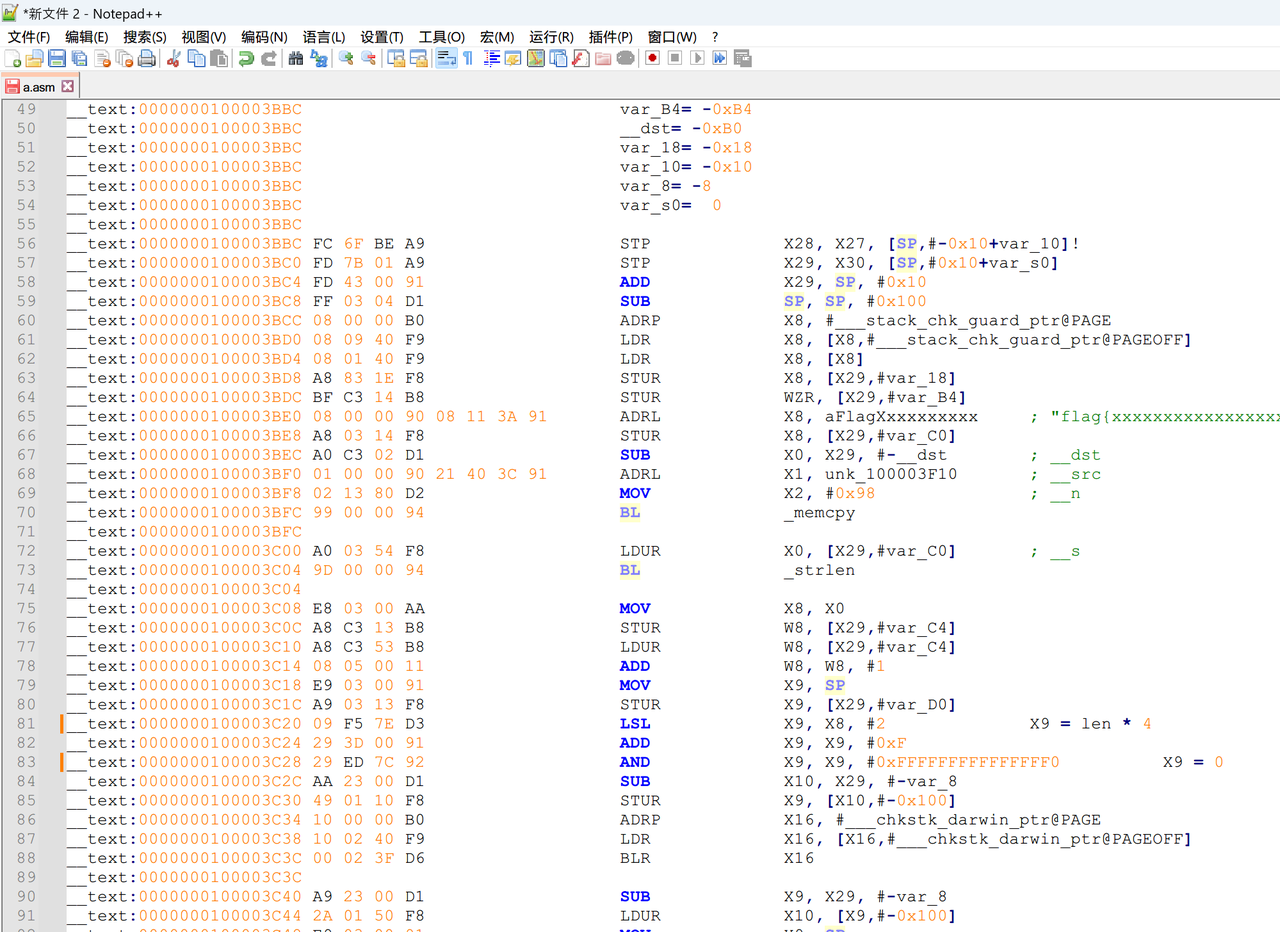
找到关键点
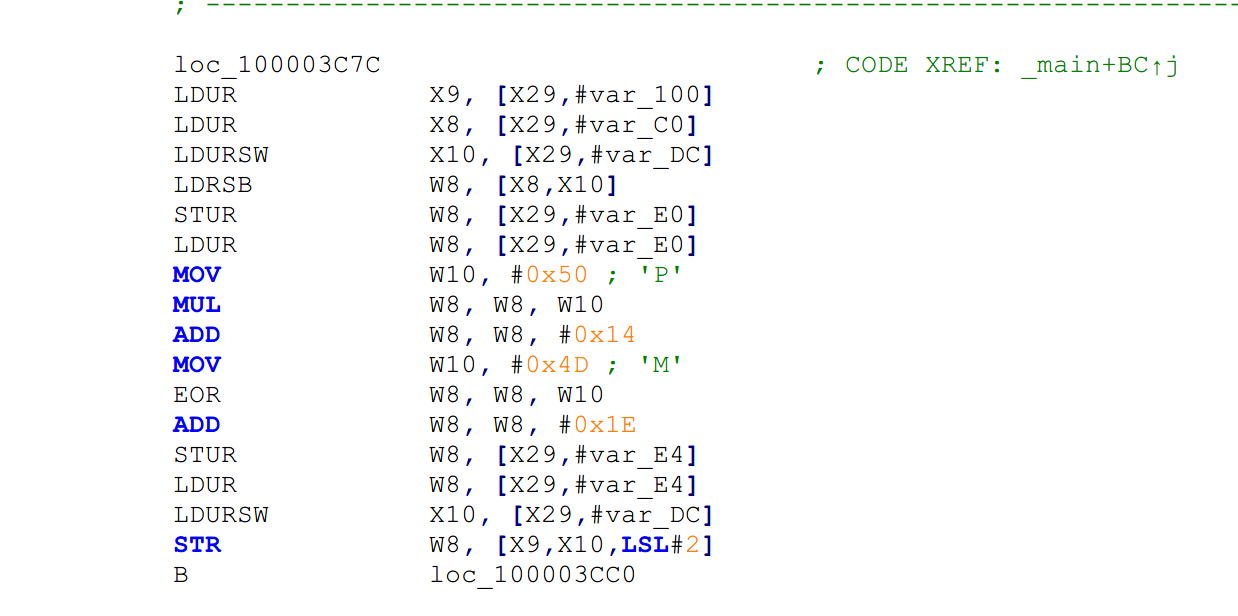
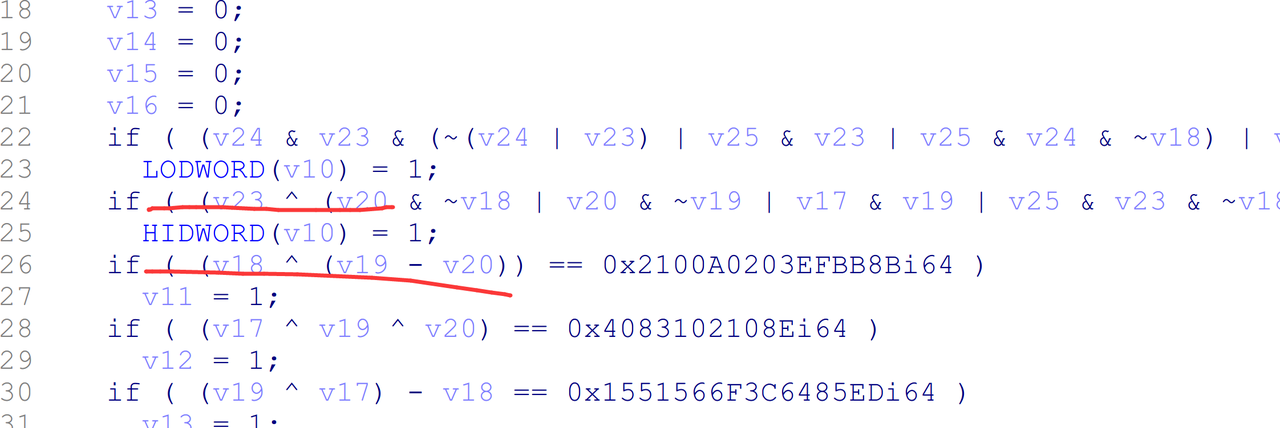
EOR就是XOR,分析得到以下算法
W8 = (W8 * 0x50) + 0x14;
W8 ^= 0x4D;x
W8 += 0x1E;
再继续分析
__text:0000000100003D88 loc_100003D88 ; CODE XREF: _main+1C8↑j
__text:0000000100003D88 A8 03 50 F8 LDUR X8, [X29,#var_100]
__text:0000000100003D8C A9 83 90 B8 LDURSW X9, [X29,#var_F8]
__text:0000000100003D90 08 79 69 B8 LDR W8, [X8,X9,LSL#2] W8 = [X8 + [X29 + var_F8] * 4]
__text:0000000100003D94 AA 83 90 B8 LDURSW X10, [X29,#var_F8]
__text:0000000100003D98 A9 C3 02 D1 SUB X9, X29, #-__dst X9 = X29 + dst
__text:0000000100003D9C 29 79 6A B8 LDR W9, [X9,X10,LSL#2] W9 = [X9 + [X29 + var_F8] * 4]
__text:0000000100003DA0 08 01 09 6B SUBS W8, W8, W9 W8 == W9
__text:0000000100003DA4 E8 17 9F 1A CSET W8, EQ
__text:0000000100003DA8 88 00 00 37 TBNZ W8, #0, loc_100003DB8
__text:0000000100003DA8
__text:0000000100003DAC 01 00 00 14 B loc_100003DB0
__text:0000000100003DAC
注意到,W8和W9相等时候正确
再找到开始的时候的memcpy
__text:0000000100003BEC A0 C3 02 D1 SUB X0, X29, #-__dst ; __dst
__text:0000000100003BF0 01 00 00 90 21 40 3C 91 ADRL X1, unk_100003F10 ; __src
__text:0000000100003BF8 02 13 80 D2 MOV X2, #0x98 ; __n
__text:0000000100003BFC 99 00 00 94 BL _memcpy
得到加密后数据(exp里面的a)
然后反向计算输出,得到exp:
a=[0x1FD7,0x21B7,0x1E47,0x2027,0x26E7,0x10D7,0x1127,0x2007,0x11C7,0x1E47,0x1017,0x1017,0x11F7,0x2007,0x1037,0x1107,0x1F17,0x10D7,0x1017,0x1017,0x1F67,0x1017,0x11C7,0x11C7,0x1017,0x1FD7,0x1F17,0x1107,0x0F47,0x1127,0x1037,0x1E47,0x1037,0x1FD7,0x1107,0x1FD7,0x1107,0x2787]
for i in a:
print(chr((((i-0x1e)^0x4d)-0x14) // 0x50),end='')
flag{67e9a228e45b622c2992fb5174a4f5f5}
androidso_re
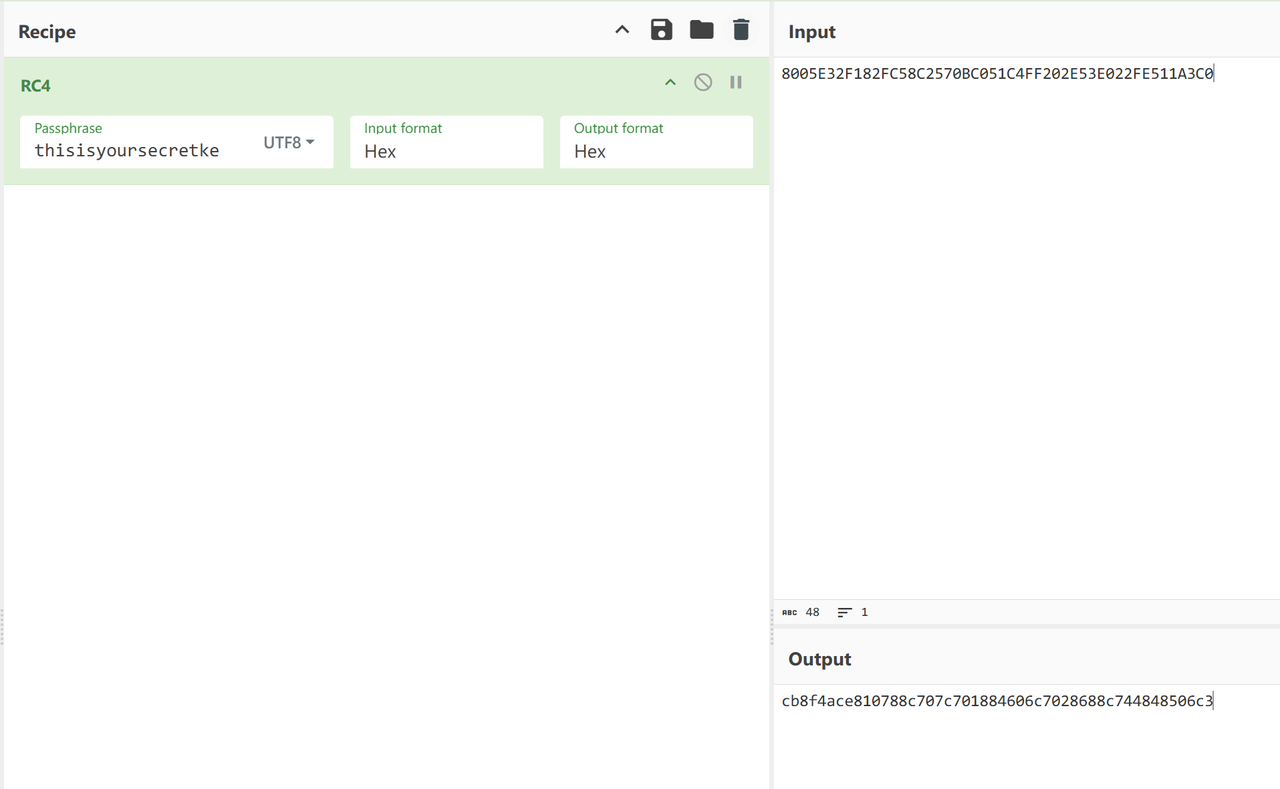
getkey:先用rc4解出enc,再异或key
Key: A8UdWaeq
https://gchq.github.io/CyberChef/#recipe=RC4(%7B'option':'UTF8','string':'YourRC4Key'%7D,'UTF8','Latin1')XOR(%7B'option':'Hex','string':'038933b8540c206a'%7D,'Standard',false)&input=VEZTZWNyZXRfS2V5&oeol=FF
Getiv:
a="F2IjBOh1mRW="
for i in range(len(a)):
if (ord(a[i])>65 and ord(a[i])<90) or (ord(a[i])>97 and ord(a[i])<127):
if ord(a[i])-65<=0x1a:
v9=65
v10=-49
elif ord(a[i])-97<0x19:
v9=97
v10=-81
print(chr(v9+(v10+ord(a[i]))%26),end="")
else:
print(a[i],end="")
#V2YzREx1cHM= IV: Wf3DLups
descbc解密即可
https://gchq.github.io/CyberChef/#recipe=From_Base64('A-Za-z0-9%2B/%3D',true,false)DES_Decrypt(%7B'option':'UTF8','string':'A8UdWaeq'%7D,%7B'option':'UTF8','string':'Wf3DLups'%7D,'CBC','Raw','Raw')&input=SnFzbEhyZHZ0Z0pyUnMyUUFwK0ZFVmR3UlBOTHN3cm55a0Qvc1pNaXZtakdSS1VNVklDL3J3PT0
flag{188cba3a5c0fbb2250b5a2e590c391ce}
rust_baby
exp
#include <iostream>
#include <vector>
#include <Windows.h>
int main()
{
char* flag = (char*)"flag{abjhgkjagshjfhasjjfhasjkfasffjfhasjkfasfffhasjkfasffgdffgf}EEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEEE";
char* res = (char*)malloc(0x114);
unsigned char a[] = {
0x50,0x81,0x92,0x93,0xB4,0x75,0x16,0xE7, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x18,0x41,0xA2,0x7B,0x4C,0x5D,0xC6,0x37, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x20,0x69,0xB2,0xC3,0x84,0x05,0x6E,0x2F, 0x04, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x78,0x19,0x32,0xF3,0xEC,0x25,0x46,0xC7, 0x05, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x40,0x49,0x72,0xFB,0xF4,0x15,0xFE,0x9F, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0xB0,0xE1,0xF2,0x53,0x14,0x9D,0xC6,0x27, 0x04, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x50,0x81,0x92,0x93,0xB4,0x75,0x16,0xE7, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x18,0x41,0xA2,0x7B,0x4C,0x5D,0xC6,0x37, 0x09, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x20,0x69,0xB2,0xC3, 0x84,0x05,0x6E,0x2F, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x78,0x19,0x32,0xF3,0xEC,0x25,0x46,0xC7, 0x09, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x40,0x49,0x72,0xFB,0xF4,0x15,0xFE,0x9F, 0x08, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0xB0,0xE1,0xF2,0x53,0x14,0x9D,0xC6,0x27, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x50,0x81,0x92,0x93,0xB4,0x75,0x16,0xE7, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
};
unsigned char b[] = {0xDC, 0x5F, 0x20, 0x22, 0xC2, 0x79, 0x19, 0x56, 0x35, 0xDA, 0x8B, 0x47, 0xD3, 0x19, 0xFC, 0x55,0x14, 0xCD, 0xD2, 0x7B, 0x58, 0x59, 0x09, 0x42, 0xDE, 0x2C, 0xB4, 0x48, 0xD9, 0xF2, 0x1B, 0xA9,0x40, 0xE1, 0xA6, 0xFB, 0xFF, 0x38, 0xC1, 0xD5, 0xE2, 0xE8, 0x77, 0x78, 0x6F, 0x22, 0x04, 0xE6,0x16, 0x3E, 0x0C, 0x35, 0x52, 0x5C, 0xFD, 0xC1, 0xE5, 0x59, 0x1C, 0xD0, 0xAE, 0x5A, 0xB2, 0xDD,0x19, 0xF8, 0x42, 0xE6, 0x2C, 0x89, 0x59, 0xE5, 0x11, 0x9C, 0xC8, 0x7B, 0x81, 0x70, 0x7F, 0x6F,0xBC, 0x6F, 0x02, 0x8F, 0xF7, 0xF4, 0xC8, 0x70, 0xAE, 0x02, 0xF8, 0x5B, 0xE2, 0x72, 0x08, 0x09,0x6F, 0xBF, 0x4B, 0x39, 0xB5, 0xD0, 0x1E, 0xA3, 0x23, 0xAB, 0x9B, 0x43, 0xB1, 0x15, 0xD7, 0xBE};
/*
int id = 0;
for (int k = 0; k < 13*8; k += 8)
{
for (int index = 0; index < 4; index++) {
DWORD p1 = a[9 + index * 2 + 16 * (k / 8)] ^ a[1 + index * 2 + 16 * (k / 8)];
DWORD p2 = a[8 + index * 2 + 16 * (k / 8)] ^ a[0 + index * 2 + 16 * (k / 8)];
DWORD col = (p1 | p2) & 0x1;
//res[id++] = (char)(flag[0 + index * 2 + 8 * (k / 8)] - col + index) ^ 0x33;
//res[id++] = (char)(flag[1 + index * 2 + 8 * (k / 8)] - col + index) ^ 0x33;
}
}
for (int i = 0; i < 0x70; i++)
{
res[i] ^= b[i];
}
*/
unsigned char c[] = { 0x8a,0x07,0x72,0x76,0x8d,0x7d,0x4d,0x51,0x35,0xde,0x88,0x16,0xd4,0x04,0xf9,0x0e,0x08,0xcf,0xcc,0x7c,0x0f,0x0d,0x09,0x5e,0xd5,0x7e,0xe4,0x4b,0xc4,0xf3,0x1c,0xaf,0x12,0xe4,0xa0,0xae,0xf6,0x69,0xc9,0xd2,0xe0,0xa7,0x01,0x0e,0x1a,0x57,0x70,0x92,0x61,0x49,0x7a,0x43,0x27,0x29,0x89,0xb5,0x92,0x2e,0x6a,0xa6,0xdb,0x2f,0xc6,0xa9,0x6e,0x8f,0x34,0x90,0x59,0xfc,0x2d,0x91,0x66,0xeb,0xbe,0x0d,0xf4,0x05,0x0b,0x1b,0xcb,0x18,0x74,0xf9,0x82,0x81,0xbc,0x04,0xd9,0x75,0x8e,0x2d,0x97,0x07,0x7c,0x7d,0x18,0xc8,0x3d,0x4f,0xc0,0xa5,0x6a,0xd7 };
for (int i = 0; i < 0x70; i++)
{
c[i] ^= b[i];
}
int id = 0;
for (int k = 0; k < 13 * 8; k += 8)
{
for (int index = 0; index < 4; index++) {
DWORD p1 = a[9 + index * 2 + 16 * (k / 8)] ^ a[1 + index * 2 + 16 * (k / 8)];
DWORD p2 = a[8 + index * 2 + 16 * (k / 8)] ^ a[0 + index * 2 + 16 * (k / 8)];
DWORD col = (p1 | p2) & 0x1;
for (int jj = 0x20; jj <= 0x7f; jj++)
{
char pp = (char)(jj - col + index) ^ 0x33;
if (pp == c[0 + index * 2 + 8 * (k / 8)])
{
res[id++] = jj;
break;
}
}
for (int jj = 0x20; jj <= 0x7f; jj++)
{
char pp = (char)(jj - col + index) ^ 0x33;
if (pp == c[1 + index * 2 + 8 * (k / 8)])
{
res[id++] = jj;
break;
}
}
}
}
std::cout << res;
return 0;
}
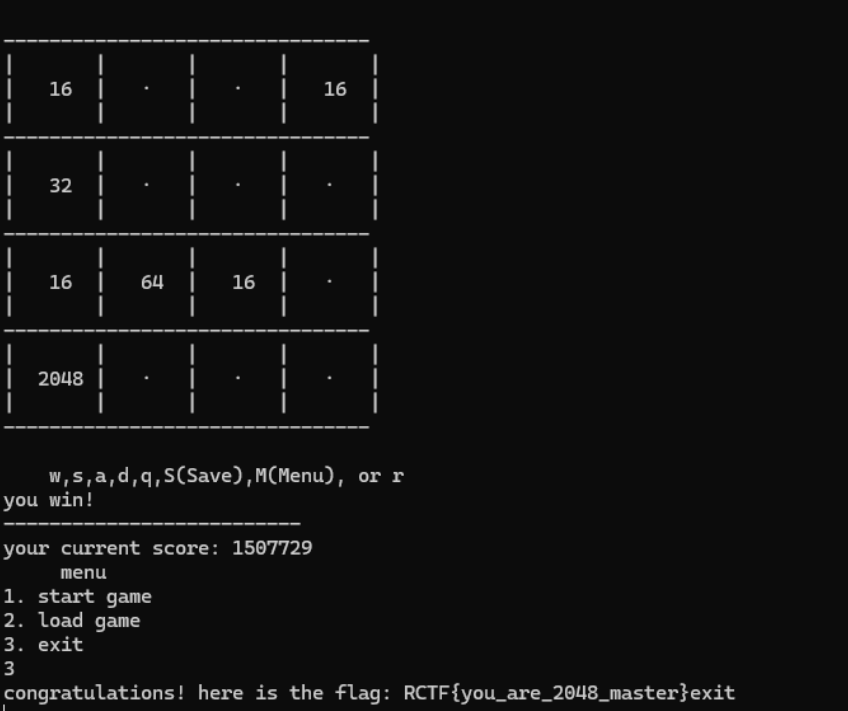
flag{6e2480b3-4f02-4cf1-9bc0-123b75f9a922}